A sophisticated strain of ransomware called Tycoon has been selectively targeting education and software companies since December 2019, according to a joint report released this week by BlackBerry and KPMG’s UK Cyber Response Services.
Because of its unique development, Tycoon can target both Windows and Linux systems and has the ability to remain hidden for long periods of time from security tools, according to the BlackBerry analysts.
One reason for Tycoon’s stealth abilities is that ransomware is written in Java and is deployed in the form of a Trojanized Java Runtime Environment. In addition, the malware is compiled in an obscure Java image file format – called Jimage – that also helps it avoid detection from security tools, according to the report.
The use of the Trojanized Java Runtime Environment means that Tycoon cannot be deployed in mass phishing emails that target as many potential victims as possible. Instead, its operators deliberately pick a target and use other means to initiate the attack, says Eric Milam, vice president of threat intelligence at BlackBerry.
Milam also notes that since Tycoon was developed in Java, it allows the ransomware to target systems other than Windows.
“To deploy this ransomware, the threat actor needs to establish a foothold into the organization enterprise, do recognizance, identify targets and gain access,” Milam told Information Security Media Group. “Developing the ransomware in platform-independent language like Java the actors can target any type of operating system with this ransomware.”
Since December 2019, Milam says BlackBerry analysts have detected about a dozen attacks related to Tycoon, although that figure could be higher.
Tycoon Attacks
Since Tycoon is not designed to be distributed through phishing or spam emails, the BlackBerry analysts believe that its operators exploit vulnerabilities in remote desktop protocols as part of the initial attack.
Other ransomware gangs are also looking for these types of vulnerabilities to exploit, and the recent surge in work-from-home environments has caused security researchers to warn organizations to better lock down and protect RDP connections.
Once the attackers gain an initial foothold, they look to maintain persistence in the network by using a technique called Image File Execution Options injection, also known as IFEO. In most cases, the IFEO settings are stored in the Windows registry and these settings give developers an option to debug their software through the attachment of a debugging application during the execution of a target application, the report notes.
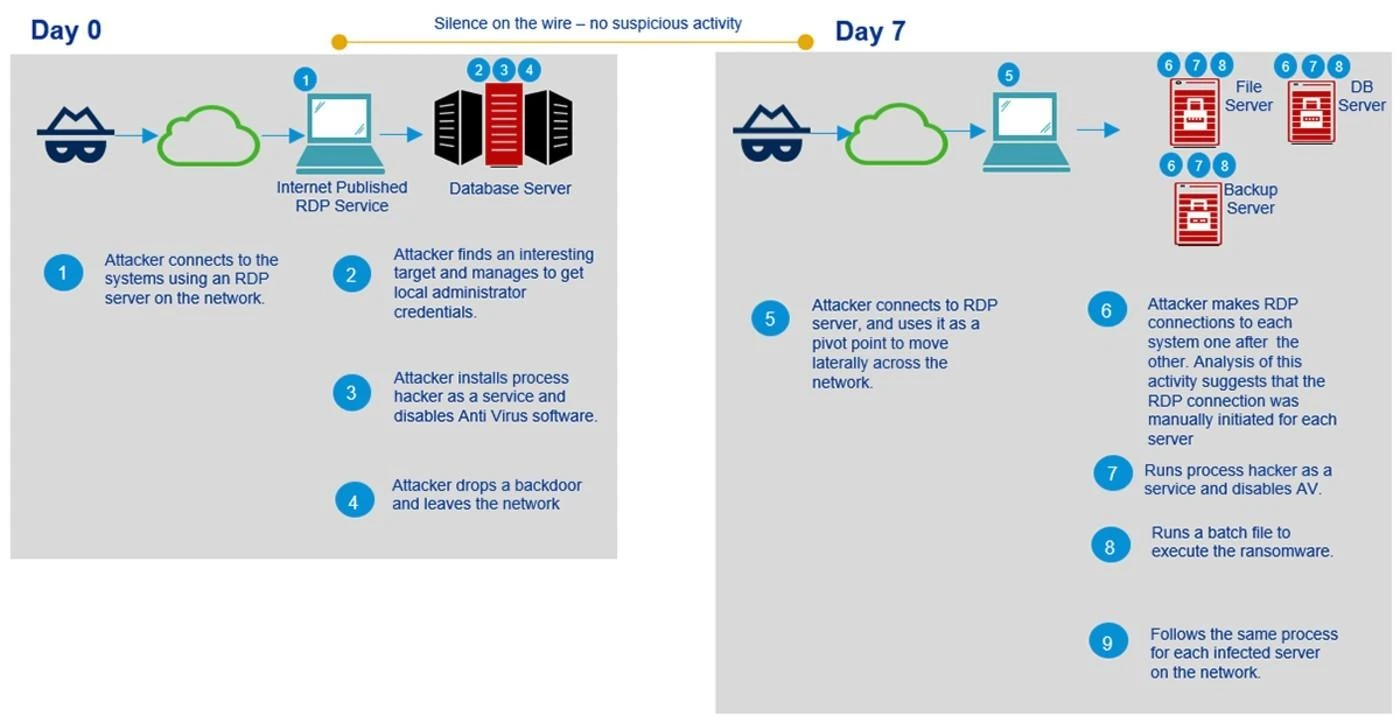
This technique then gives the attackers additional privileges within the infected network and allows them to install a backdoor, disable anti-malware software and change passwords in Windows Active Directory, according to BlackBerry.
Finally, the Tycoon ransomware is delivered in a zip archive file that contains the Trojanized Java Runtime Environment build as well as the Jimage file that helps the malware avoid detection, the report notes. After that, the ransomware encrypts certain files.
The BlackBerry team was able to analyze how this attack worked after conducting a forensic audit of one victim.
“The ransomware was deployed in a targeted attack against an organization, where the system administrators had been locked out of their systems following an attack on their domain controller and file servers,” Milam says.
“After conducting forensic investigations of the infected systems it became apparent that the initial intrusion occurred via an internet facing RDP jump-server. Once the victim systems were identified and access gained, the threat actor had all the means to download and deploy the custom Java Runtime Environment build with the ransomware baked in.”
Ransom Note and Decryption
The BlackBerry report also contains a copy of the ransom note, where the operators of Tycoon demand payment in bitcoin, and the victim has 24 hours to respond or the price will increase. The cybercriminals also offer a free test of their decryption tool to entice the victim to pay.
In an effort to counter Tycoon attacks, security firm Emsisoft has released its own free decryption tool for this ransomware. This tool, however, only works with the original variant of the ransomware called RedRum.
BlackBerry’s Milam warns that organizations are now more likely to see ransomware such as Tycoon and PonyFinal, which are developed in Java and designed for more targeted attacks.
“There have been other attacks we’ve seen that exploit Java but Tycoon is the first one we’ve seen that is using the custom format – Jimage – that is mostly used natively in the Java Developer Kit,” Milam tells ISMG.
“All the Java malware seen up until now was delivered using the well-known Java Archive format. Jimage is mostly undocumented, as it’s supposed to be internal to the Java Developer Kit, so it’s likely we’ll see more of this ransomware emerge now that we know it exists.”



