Apple will be introducing quantum computer protection for iMessage with the release of iOS 17.4, which Apple describes as the “most significant cryptographic security upgrade in iMessage history,” and it will apply to iPhones as well as iPads and Macs.
PQ3 is the first messaging protocol to reach Level 3 security — providing protocol protections that surpass those in all other widely deployed messaging apps.
Last fall, Signal announced an update to protect users from the future risk that tomorrow’s quantum computing will likely break today’s encryption. And while this is years down the road, the new techniques could be applied to today’s content if that has been captured and stored for that purpose—known as harvest now, decrypt later.
te to protect users from the future risk that tomorrow’s quantum computing will likely break today’s encryption. And while this is years down the road, the new techniques could be applied to today’s content if that has been captured and stored for that purpose—known as harvest now, decrypt later.
Signal’s PQXDH introduced the first system to protect the cryptographic keys used to encrypt messaging between users from being compromised.
“The systems known to exist today,” Signal warns, “do not yet have enough qubits to pose a threat to the public-key cryptography that Signal currently uses. However, if a sufficiently powerful quantum computer were built in the future, it could be used to compute a private key from a public key thereby breaking encrypted messages.”
The solution, it says, is “a new post-quantum cryptosystem… to implement new one-way functions that cannot be advantageously reversed by a quantum computer.”
Apple agrees with the threat assessment, warning that “a sufficiently powerful quantum computer could solve the classical mathematical problems in fundamentally different ways, and therefore—in theory—do so fast enough to threaten the security of end-to-end encrypted communications.”
Apple says it is now delivering “the strongest security properties of any at-scale messaging protocol in the world.” Not only is it matching Signal’s update, but Apple says it is going further and has rebuilt iMessage’s entire encryption protocol—ground up—to deliver this.
Apple describes Signal’s update as Level 2, an advance on the Level 1 security which is used by WhatsApp, Facebook Messenger, Google Messages, and Signal and iMessage before these recent updates.
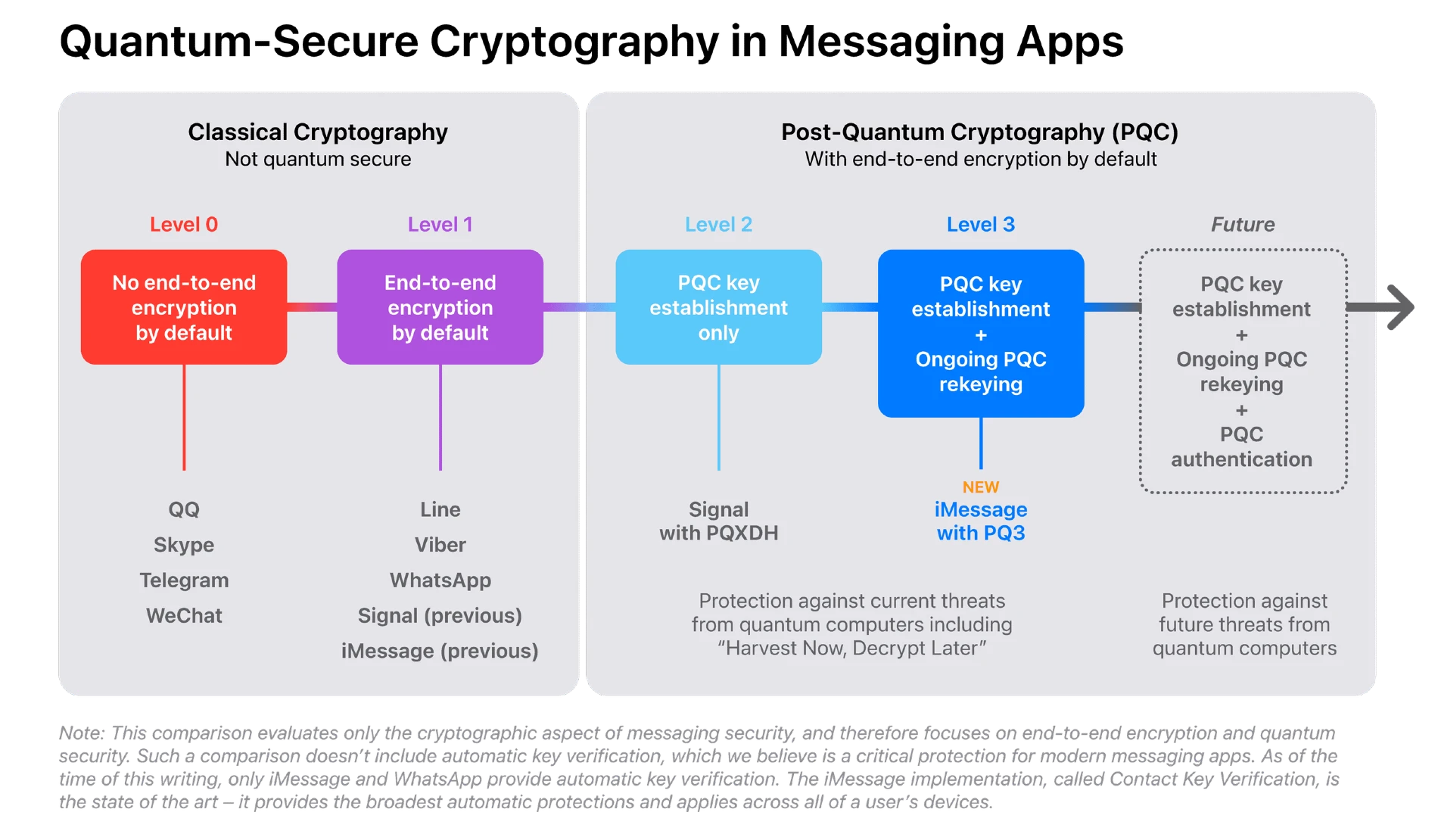
Apple says iMessage is now moving to a new Level 3. The risk, it says, is that Signal only protects an initial key exchange. If a key is captured and later decrypted, then all subsequent content could potentially be compromised. Level 3 adds periodic, post-quantum protected key changes, meaning if a key is captured and later compromised, it will only expose a limited timeframe of content, until that key changed.
Historically, messaging platforms have used classical public key cryptography, such as RSA, Elliptic Curve signatures, and Diffie-Hellman key exchange, to establish secure end-to-end encrypted connections between devices.
All these algorithms are based on difficult mathematical problems that have long been considered too computationally intensive for computers to solve, even when accounting for Moore’s law.
However, the rise of quantum computing threatens to change the equation. A sufficiently powerful quantum computer could solve these classical mathematical problems in fundamentally different ways, and therefore — in theory — do so fast enough to threaten the security of end-to-end encrypted communications.
Although quantum computers with this capability don’t exist yet, extremely well-resourced attackers can already prepare for their possible arrival by taking advantage of the steep decrease in modern data storage costs.
The premise is simple: such attackers can collect large amounts of today’s encrypted data and file it all away for future reference. Even though they can’t decrypt any of this data today, they can retain it until they acquire a quantum computer that can decrypt it in the future, an attack scenario known as Harvest Now, Decrypt Later.
To mitigate risks from future quantum computers, the cryptographic community has been working on post-quantum cryptography (PQC): new public key algorithms that provide the building blocks for quantum-secure protocols but don’t require a quantum computer to run — that is, protocols that can run on the classical, non-quantum computers we’re all using today, but that will remain secure from known threats posed by future quantum computers.
Support for PQ3 will start to roll out with the public releases of iOS 17.4, iPadOS 17.4, macOS 14.4, and watchOS 10.4, and is already in the corresponding developer preview and beta releases. iMessage conversations between devices that support PQ3 are automatically ramping up to the post-quantum encryption protocol.



