ExtraHop has expanded decryption support for Microsoft authentication and application protocols, providing high-fidelity detection of malicious activity associated with nearly two-thirds of the most exploited network protocols.
ExtraHop is a cybersecurity company that is the leader in cloud-native Network Detection and Response (NDR) are expanding its decryption capabilities to Microsoft environments.
The decryption technology from ExtraHop is the first for the industry. It detects the new class of advanced attacks exploiting proprietary Microsoft protocols which evade security controls and traditional monitoring tools like next-generation firewalls and web proxies.
This first-and-only decryption capability detects a new class of advanced attacks, including ‘living-off-the-land’ and Active Directory Kerberos Golden Ticket attacks, that exploit proprietary Microsoft protocols to evade security controls and traditional monitoring tools like next-generation firewalls (NGFW) and web proxies.
Advanced decryption also detects high risk CVE exploitation such as PrintNightmare, ZeroLogon, and ProxyLogon, and provides proactive defense against future zero-day exploits.
“In 2021, the sophistication of ransomware has increased significantly, with techniques that were once the sole purview of nation states now regularly being used for illicit financial gain,” said Jon Oltsik, Sr. Principal Analyst, ESG Research.
“This new class of attacks, including Living-off-the-Land and Active Directory Golden Ticket, exploit organizations’ biggest blind spot––encrypted traffic. ExtraHop has long supported secure decryption of east-west SSL and TLS 1.3 traffic, and can now extend that support for critical Microsoft protocols at the center of today’s most insidious attacks.”
According to a Joint Cybersecurity Advisory issued by the U.S. FBI, CISA, the UK National Cyber Security Centre, and the Australian Cyber Security Centre, encrypted protocols such as Microsoft Server Message Block v3 are used to mask lateral movement and other advanced tactics in 60% of the 30 most exploited network vulnerabilities. Of the top 11 most exploited vulnerabilities, four involve Microsoft systems. Three of those four can be exploited via an encrypted channel.
Unlike NGFW and web proxies, ExtraHop Reveal(x) 360 detects sophisticated emerging attack techniques with line-rate decryption of the most commonly abused Microsoft protocols such as SMBv3, Active Directory Kerberos, Microsoft Remote Procedure Call (MS-RPC), NTLM, LDAP, WINRM, in addition to TLS 1.3.
This decryption capability also detects post-compromise activity that encrypted traffic analysis (ETA) misses, including ransomware campaigns that exploit the PrintNightmare vulnerability.
“Organizations are blind to encrypted malicious activity happening laterally within the east-west corridor,” said Sri Sundaralingam, VP, Security and Cloud Solutions at ExtraHop.
“Even technologies like firewalls and encrypted traffic analysis that claim to provide visibility fail to detect attacks that use encrypted communications to exploit vulnerabilities commonly seen in advanced threat campaigns.
ExtraHop Reveal(x) 360 can identify—with fidelity—exploitation and protocol abuse associated with major CVEs, both today and in the future.”
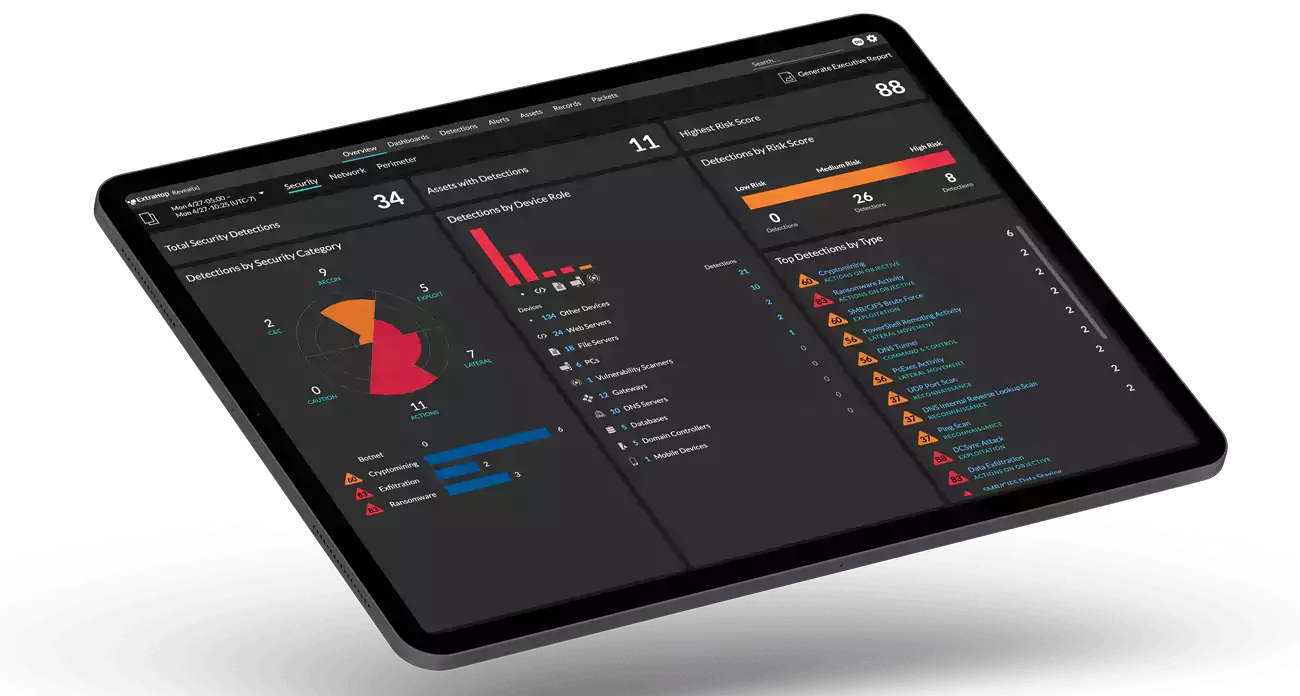
ExtraHop Reveal(x) 360
ExtraHop Reveal(x) 360 goes far beyond the limited protocol identification and statistical analysis offered by NGFW, web proxies, and ETA, securely decrypting and fully parsing Microsoft Active Directory authentication protocols (Kerberos and NTLM) and Microsoft Windows application-level protocols using passive, out-of-band decryption for rapid and accurate detection of advanced threat activity.
Reveal(x) 360 takes a SaaS-based approach to delivering NDR for hybrid and multicloud deployments. To start using Reveal(x) 360, simply identify environments you want to secure and deploy a Reveal(x) 360 sensor to gain unified visibility in a single management pane—accessible from anywhere.
ExtraHop sensors decrypt and analyse network traffic, using cloud-scale machine learning, for behavioural analysis, real-time threat detection, and investigation performed in Reveal(x) 360.
ExtraHop ML allows for a wide range of intelligent responses, including taking automated action on compromised workloads, domains, and IP addresses. You can also leverage on-demand pricing for a cloud-based record warehouse that enables index record search, query, and drill-down investigation in every segment of your hybrid environment for situational intelligence. Reveal(x) 360 also offers additional continuous packet capture (PCAP) for forensics.
Reveal(x) 360 also provides forensic-level record data on encrypted traffic, including specific SQL queries, commands sent via MS-RPC, and LDAP enumeration behaviour for comprehensive investigation and response. With Reveal(x) 360, customers can:
- Prevent unauthorized access and privilege escalation attempts via Microsoft Active Directory infrastructure.
- Monitor for ‘living-off-the-land’ tactics used during east-west lateral movements to expose hidden threats.
- Defend against high risk vulnerabilities like PrintNightmare and Microsoft Active Directory being exploited in advanced threat campaigns to carry out disruptive attacks.