Google has detailed how Triada malware continues to infect Android devices despite efforts to resolve this issue over the last few years.
Kaspersky Lab first discovered the Triada malware back in 2016, and cybersecurity experts describe the software as a rooting trojan, which means that the software exploits the device by gaining access to sensitive portions of the operating system.
This software installs spam apps downloaded from a command and control server. These spam applications display advertisements on the device and the developers of the malware gain revenue when users click on the show ads.
Aside from installing apps, Triada malware also inserts codes to four different browsers, allowing the malware to replace the ads shown on websites with advertisements that gain revenue for the malware developers. Among the affected browsers include AOSP, 360 Secure, Cheetah, and Oupeng browsers.
The software also takes advantage of a mechanism called weight watching to ensure that the device has sufficient space for the spam apps that the malware will install. This mechanism rates a file or an app depending on the date of the app installation and the certificate used to sign the software.
Apps that did not come pre-installed with the device will be among the first files to be removed to make way for the spam apps that the malware will install.
However, improvements made to the Google Play Protect allowed the search giant’s software to detect the malware automatically. Furthermore, improvements made to the Android operating system limited the impact of the malicious software to devices running older versions of Google’s OS.
Nonetheless, developers of Triada malware found a new way to infect devices, with the malicious software getting distributed even before the handsets are shipped.
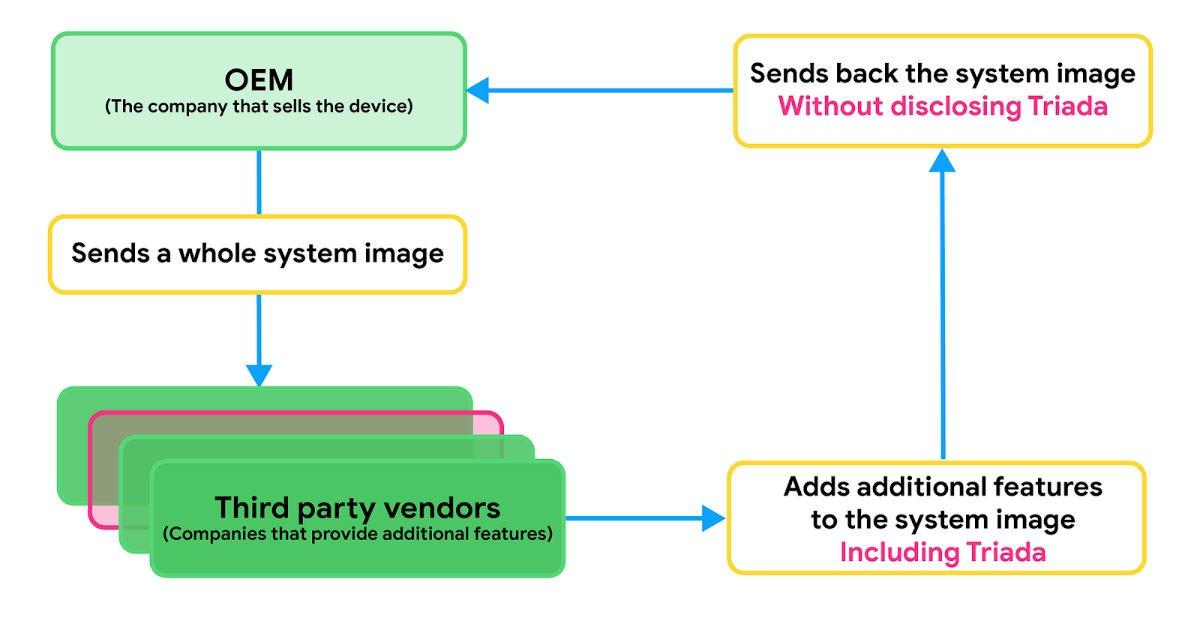 The infection occurs as third-party vendors add additional features to the proprietary skin of OEMs, and among the files that these vendors introduce to the system image is the Triada malware. These vendors return the modified system image to the handset manufacturer, although these third-party firms fail to disclose that it had included malicious software into the system image.
The infection occurs as third-party vendors add additional features to the proprietary skin of OEMs, and among the files that these vendors introduce to the system image is the Triada malware. These vendors return the modified system image to the handset manufacturer, although these third-party firms fail to disclose that it had included malicious software into the system image.
Aside from changes in how the malware infects the device, there are also changes made to how the Triada malware works. With the newer versions of the software, Triada now injects code to the Google Play application. This tactic allows the malware to install applications and make them look like the apps came from the Google Play Store.
This method also permits the malware to install apps without the need to change device settings and activate the “Installation from Unknown Sources” option. However, in reality, these applications came from the command and control server operated by the malware developers.
To resolve this problem, Google had to coordinate with OEMs to roll out updates that remove files associated with the Triada malware. To prevent future instances of malware distribution, the search giant is also offering its Build Test Suite to handset makers.



