[vc_row][vc_column][vc_column_text]BlackBerry Senior Vice President, General Manager, Mobility Solutions, Alex Thurber has revealed that the company is currently in talks with various global smartphone makers to provide its version of a secure Android operating system under a licensing deal as part of the second phase of its licensing strategy.
The company is reportedly to name its operating system BlackBerry Secure, which will come with all security features that are available with a BlackBerry-branded smartphone.
Thurber told ET,
“We have a number of different contracts that we are working on right now. We expect some to be announced soon,”
“We have an agreement with Optiemus for the India market for BlackBerry Secure.”
Under this licensing deal, a smartphone manufacturer will be able to launch its own-branded smartphone with the security features and secure private version of Android operating system by the Canadian company.
The company also sees huge opportunity in the Enterprise of Things (EoT) segment and is looking at providing its secure operating system for televisions, wearables and medical devices.
Thurber said.
“We have already started talking to a couple of medical manufacturers. John Chen had also talked about TVs – there is an amazing amount of products that run Android and since we are able to make a very secure Android, we think there are a lot of opportunities. We have a very specific plan and we are working to that plan,”
“We believe it is important to bring security into every element of enterprise of things,”
What this effectively means is that instead of having to buy a BlackBerry-branded device to get their version of a secure OS, it will be possible to buy devices from other manufactures.[/vc_column_text][vc_column_text]
BlackBerry Secure
When Android first made its way into the consumer market, no one could have predicted the impact it would have. Android was an operating system developed with a simple idea at its core: Google’s founders wanted smarter mobile devices that better served their users.
Today, that simple idea has helped make Android the most popular mobile OS on the market, with a global share of 66% and rapidly rising.
Android’s popularity can largely be traced to its sheer diversity. Almost from the beginning, it has been an open platform, and there are countless devices from countless manufacturers that users can choose between.
Therein lies the problem – due to its widespread popularity, Android finds itself targeted by criminals and malware with greater frequency than any other operating system. This means that although the OS is not inherently vulnerable, any vulnerabilities that do exist tend to be exploited if they aren’t patched in a timely fashion. Moreover, because so many different vendors count themselves as players in the Android space, it’s inevitable that some will lag behind with security patching.[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]In the meantime, their devices will remain vulnerable, even as they’re being used to handle sensitive business data.
“Nearly every organization supporting smartphones and tablets must have a strategy to support Android devices, despite some of the security challenges,” reads a recent white paper by J. Gold Associates.
“As we moved to a more mobile world over the past several years, the number of potential attack points increased dramatically, and many of them consisted of user-selected and often unsecured devices as a byproduct of BYOD,” the paper continues.
“The ability to secure data and prevent corporate breaches consistently ranks among the top issues both IT and general management struggle with on a regular basis. A February 2016 Ponemon Institute survey shows that 67% of companies are either certain or very likely to have had a security breach due to a mobile device.”
Slow security patching is far from the only threat facing Android within the enterprise. To grant themselves additional freedoms and run certain applications, many users choose to root their devices, stripping away core security functionality in the interest of personalization. And though measures such as Samsung KNOX and Android for Work exist to separate corporate and private data, these software solutions can be fooled by a savvy enough user.
What is Rooting?
“Rooting” refers to the process by which a mobile user alters or replaces system applications or settings which are ordinarily inaccessible to them, sometimes even replacing the operating system entirely.
That’s where BlackBerry comes in. Security has always been in BlackBerry’s blood, and the company has always made it a priority to protect both clients and their data. That’s why the company made their own foray into the Android device market, bringing their full security expertise to bear.
BlackBerry has long set the bar for mobile security, and their approach to Android is no different.
Other mobile device vendors can take weeks or months to release patches. Along with Google’s Pixel devices, BlackBerry has a record of being the quickest device manufacturer on the market to deliver security updates.
When Google releases its security bulletin each month, BlackBerry sends out a Security Maintenance Release to address any flagged vulnerabilities. The company also provide as-needed hotfixes for critical vulnerabilities outside those maintenance windows, such as their fixes for the Quadrooter vulnerability.[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]
Dedicated Security Response Teams
Providing world-class security has always been a significant area of focus for BlackBerry, which is why they have several teams dedicated to security:
The BlackBerry Security Incident Response Team (BBSIRT) ensures that public and private reports of vulnerabilities are quickly received, analysed, and mitigated to protect their clients. This team collaborates with customers, partners, vendors, governments, academics, and security researchers to monitor and address the Android threat landscape 365 days a year.
The Security Research Group is a global team of ethical hackers whose mandate is to identify security issues in the BlackBerry product portfolio and work closely with development teams to resolve them. They also conduct active research into advanced security threats and defensive technologies.
Security works best if it meshes with what the employees want – it’s most effective when it’s not inconvenient to connect to a security solution or use a device.[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]
Device Security Built in from The Start
Improving the integrity of the Android OS is a cornerstone of BlackBerry’s approach to securing Android. To that end, the company has incorporated many improvements to Android’s core security, locking down device capabilities that could give attackers the opportunity to compromise a device – and in so doing, your organization. From the Hardware Root of Trust to their own enhanced bootloader, everything about BlackBerry Android devices is architected to protect your data, both corporate and personal.
The Hardware Root of Trust
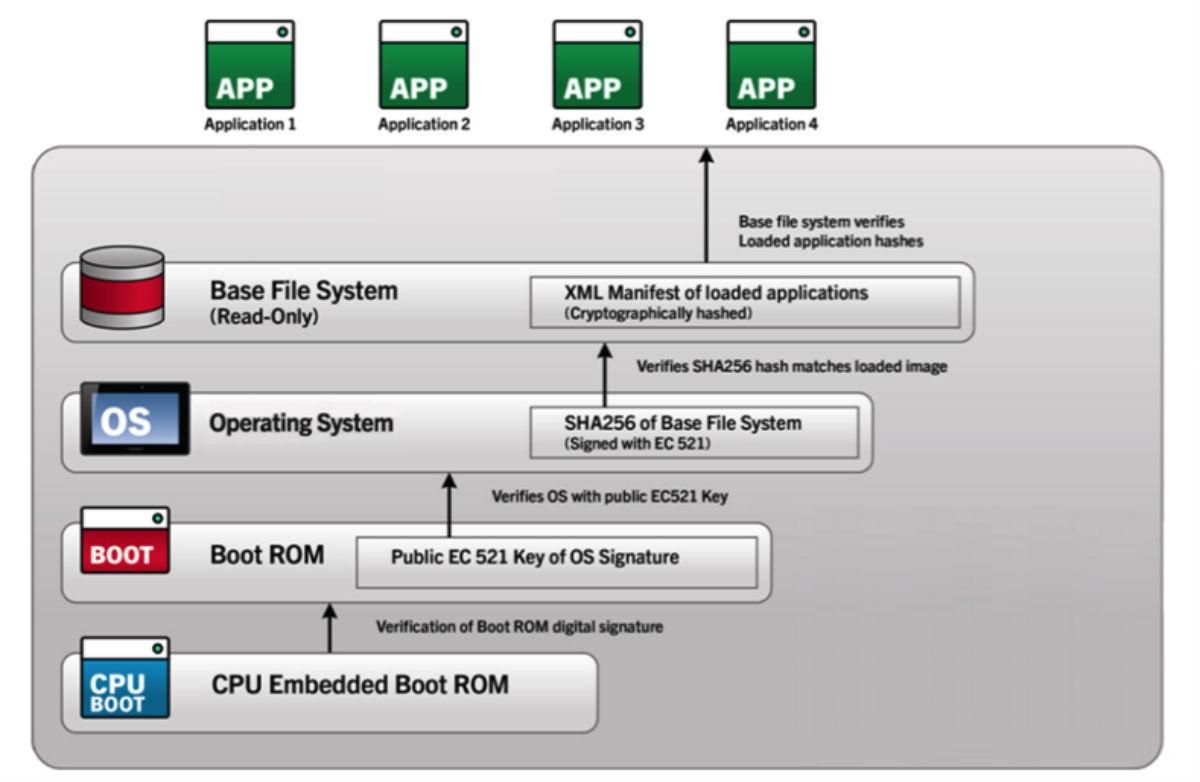
Rather than layering on defenses after production, BlackBerry has built security into their Android OS from the start. The manufacturing process makes use of the Hardware Root of Trust, a proprietary technique that adds security keys to the device processor as it’s built. These keys are then used to track, verify, and provision each device, ensuring their authenticity and integrity are guaranteed – along with the safety of the data they contain.
In addition to serving as the foundation of the company’s other security measures, the Hardware Root of Trust acts as a safeguard against counterfeiting, which could expose your organization to a wide range of malware.
BlackBerry’s Secure Bootloader
Built upon the Hardware Root of Trust, the secure boot chain in BlackBerry’s Android makes use of multiple verification stages to ensure that the device has not been tampered with. Each stage of the secure boot chain must verify that the next component is intact before proceeding. This further protects devices against tampering and ensures that rooted devices – and the security risks they represent – are not present in your organization.[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]
BlackBerry Integrity Detection
BlackBerry Integrity Detection continuously monitors for events or configuration changes that may indicate a device’s security is compromised. It integrates readily with EMM and third-party monitoring solutions, so that when a suspicious modification is detected it’s easy to generate integrity reports and automated responses to compromised devices.
Android OS Hardening
BlackBerry has strengthened Google’s own Android security enhancements (Android for Work, user profile controls, etc.) with several of their own. For example, improved Address Space Layout randomization scrambles the operating system’s code to make it harder for attackers to locate vulnerabilities. BlackBerry has also hardened the Android kernel, removing unnecessary functionality which would otherwise render the operating system vulnerable.
FIPS 140-2 Compliant Full Disk Encryption
BlackBerry Powered Android devices protect their data with full-disk encryption, which is turned on automatically and cannot be disabled. BlackBerry further enhances the protections provided by this encryption through the use of a FIPS 140-2 compliant kernel. This is the same sort of encryption employed by the United States government, and allows the company’s devices to be readily used in regulated industries; encryption keys are cordoned off within BlackBerry Secure Compound and fully write-protected. This means that even if a device is lost or stolen, your information is safe.
Security often seems complicated, obtuse, and troublesome for both the administrator and the end user – but it doesn’t need to be. BlackBerry’s Android is designed to give the end user visibility and control of their data, while BlackBerry make your corporate devices more secure by making security both painless and convenient.
[/vc_column_text][/vc_column][/vc_row][vc_row][vc_column][vc_column_text]
Other Security Features
BlackBerry’s Android offers a number of other diverse security options, including:
- Media Card Protection: Users control who can access a device’s media card, protecting the information stored there and further separating work and personal profiles.
- Remote Device Management: Lost or stolen devices can be located through GPS positioning, and they can also be remotely locked and wiped.
- Application Sandboxing: On BlackBerry’s Android, applications are isolated to their own area of the device, and sandboxed off from one another to minimize the damage that might be caused by a rogue app.
- Data-in-transit protection: Information traveling over Wi-Fi, VPN, Bluetooth, and NFC connections is fully encrypted.
[/vc_column_text][/vc_column][/vc_row]




