At Black Hat USA 2020 Monday, BlackBerry released a free open-source tool for cybersecurity professionals, called PE Tree that significantly reduces the time and effort required to reverse engineer malware.
Reverse engineering of malware is an extremely time- and labor-intensive process, which can involve hours of disassembling and sometimes deconstructing a software program.
The BlackBerry Research and Intelligence team initially developed this open source tool for internal use and is now making it available to the malware reverse engineering community.
“The cybersecurity threat landscape continues to evolve and cyberattacks are getting more sophisticated with potential to cause greater damage,” said Eric Milam, Vice President of Research Operations, BlackBerry.
“As cyber-criminals up their game, the cybersecurity community needs new tools in their arsenal to defend and protect organisations and people. We’ve created this solution to help the cybersecurity community in this fight, where there are now more than 1 billion pieces of malware with that number continuing to grow by upwards of 100 million pieces each year.”
The PE Tree enables reverse engineers to view Portable Executable (PE) files in a tree-view using pefile and PyQt5, thereby lowering the bar for dumping and reconstructing malware from memory while providing an open-source PE viewer code-base that the community can build upon.
The tool also integrates with Hex-Rays’ IDA Pro decompiler to allow for easy navigation of PE structures, as well as dumping in-memory PE files and performing import reconstruction; critical in the fight to identify and stop various strains of malware.
BlackBerry will also be presenting a sponsored webinar about its partnership with Intel to stop cryptojacking malware, and drill down into BlackBerry Optics AI-based EDR technology for Linux.
Also this week at Black Hat USA 2020, Kevin Livelli, BlackBerry’s Director of Threat Intelligence will be presenting on Decade of the RATs on August 5 at 11-11:40 am PT.
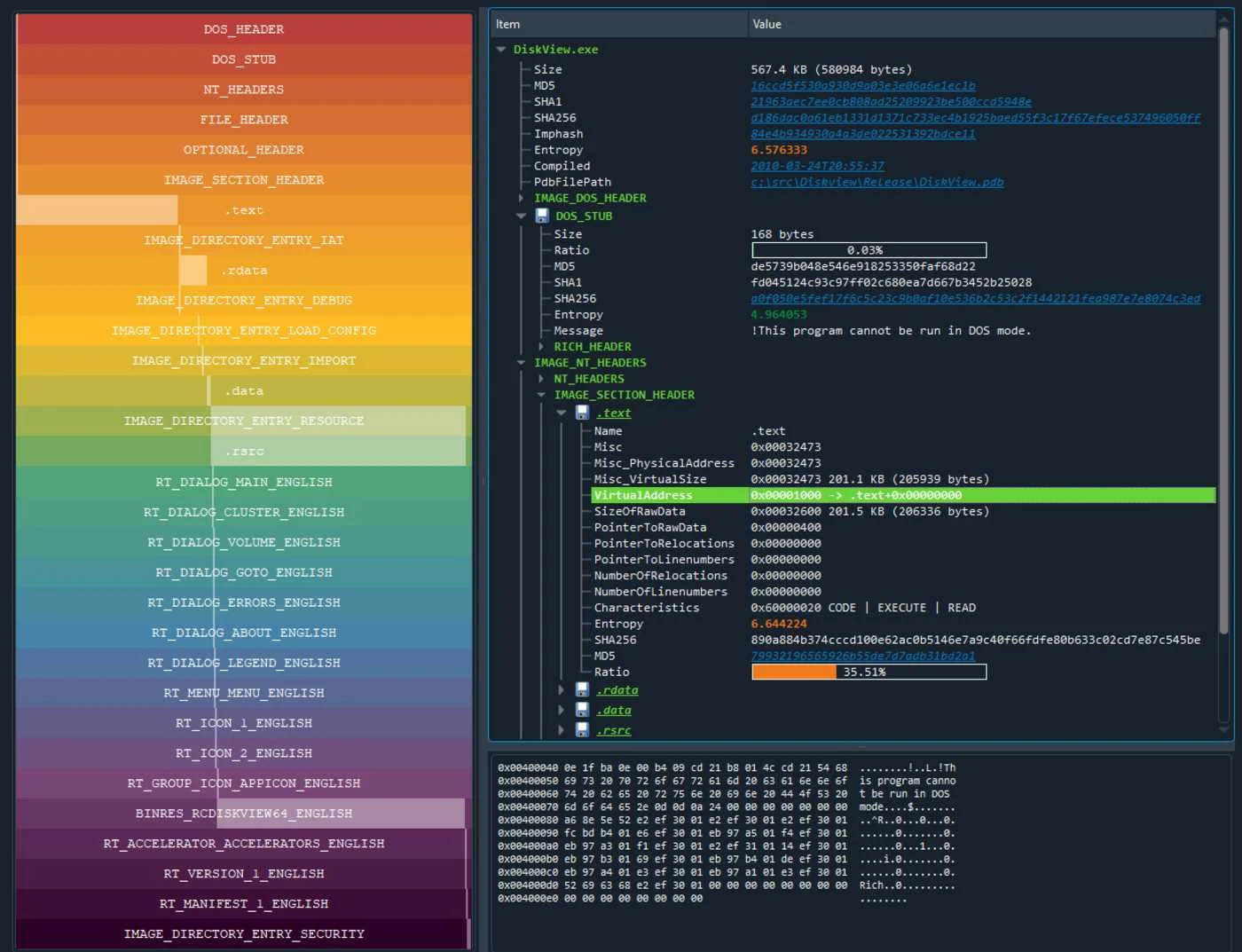
PE Tree
PE Tree was developed in Python and supports the Windows, Linux, and Mac operating systems. It can be installed and run as either a standalone application or an IDAPython plugin, allowing users to examine any executable Windows file and see what its composition is.
PE files are parsed using Ero Carrera’s pefile module before being mapped into a tree-view, providing a summary of the following headers: MZ header, DOS stub, Rich headers, NT/File/Optional headers, Data directories, Sections, Imports, Exports, Debug information, Load config, TLS, Resources, Version information, Certificates and Overlay.
Any highlighted links can be clicked to perform a search in VirusTotal, including File hashes, PDB path, Timestamps, Section hash/name, Import hash/name, Export name, Resource hash and Certificate serial.
In addition, certain portions of the PE file can be saved or exported to CyberChef for further processing, such as DOS stub, Sections, Resources, Certificates and Overlay.
BlackBrry says PE Tree remains under active development, so expect to see new features frequently. The next major release will focus on rekall support, offering the ability to view and dump processes from either a memory dump or live system.
PE Tree is free and open source and you can download it from Github here.




