BlackBerry Cylance has successfully completed the MITRE ATT&CK APT29 evaluation. BlackBerry Unified Endpoint Security (UES) solutions were examined for their ability to detect sophisticated tactics and techniques used by APT29, a group that cybersecurity experts believe operates on behalf of the Russian government.
MITRE developed and maintains ATT&CK based on open source reporting of adversary tactics and techniques. ATT&CK is freely available and is widely used by defenders in industry and government to find gaps in visibility, defensive tools and processes as they evaluate and select options to improve their network defense.
The MITRE ATT&CK framework is a global knowledge base of threat actor’s tactics and techniques drawn from real-world cyber attacks. Test results showing how vendor’s solutions fare against known adversaries are publicly posted to the MITRE website.
“BlackBerry security products are designed to help protect enterprises and governments from the most sophisticated threats. MITRE’s ATT&CK evaluations allow us to collaborate with the industry and demonstrate how our AI-powered solutions excel against advanced techniques, including APTs,” said Thomas Pace, VP Global Enterprise Solutions at BlackBerry.
“As APT29 was strictly a detection evaluation, it is also important to note that the core functionality of BlackBerry® Protect would have automatically prevented the attacks in their tracks at the outset, thus relieving the burden on the EDR team entirely.”
BlackBerry’s approach to the evaluation was supported by a tightly integrated portfolio of products that work together to effectively detect threats. These products enable endpoint detection and response (EDR) practitioners to reap the synergistic benefits from the immediate identification and clear context of suspicious activity.
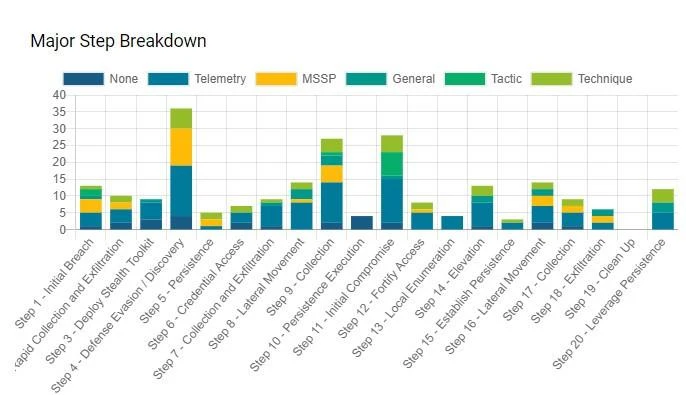
This was showcased in the APT29 test as multiple BlackBerry detections were triggered for a single threat technique.
Key results include:
- BlackBerry UES automation capabilities drastically reduce the need for manual intervention during incident response.
- BlackBerry Protect, BlackBerry Optics and BlackBerry Guard all played a key role in detecting the attacks and providing rich context about the attacks by mapping them to tactics and techniques or providing telemetry.
- BlackBerry performed extraordinarily well in terms of number of detections, far surpassing traditional EDR players.
- The APT29 evaluation validates the EDR market’s demand for new sensors included in the BlackBerry Optics 2.4 release.
- With the new sensors, BlackBerry provided visibility throughout the kill chain, and in 115 of 134 tertiary steps.
APT29 Evaluation Environment
The evaluations are performed in Microsoft Azure Cloud. Each vendor is provided an environment consisting of seven hosts on which to install their client software. The vendors also have the option of installing server software onto a virtual machine (VM) already in the environment, or importing a VM if necessary.
By default, the Azure VMs were Standard B4MS, each with four vCPUs and 16GB memory. Each vendor had full and complete administrative access to the hosts instantiated for them.
All machines are in an isolated domain in their own resource group in their own virtual network. VPN access enables connectivity to the environment, and passwords are shared via out-of-band methods. There is one VPN server per environment and vendors then RDP elsewhere within the environment.
Hosts are reachable only within the VPN. They do not have public IP addresses assigned to them via Azure, but they are able to access the Internet. After VMs are created, an additional script is kicked off to connect the VMs to the domain.
Cybersecurity vendors may apply to participate in the next round of the ATT&CK Evaluations, which will feature the Carbanak and FIN7 threat groups as the emulated adversaries, via evals@mitre-engenuity.org.



